Want to know more about how to protect yourself from Cryptolocker and increase best practices for Cybersecurity?
In this article you will learn:
- Common methods of crypto infections
- 4 Common methods of prevention
- 6 Advanced methods of prevention
- *Bonus Offer advanced secrets on Cyptolocker prevention
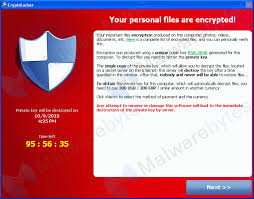
Security, more specifically Cybersecurity, is quickly becoming a hot topic of concern for many businesses. Browsing the internet has never been without certain risks however, each year our usage of web based content and services introduces increased exposures at an alarming rate. Gone are the days of the common virus that could be cleaned with a simple antivirus application or a malware infection that merely annoys your browsing experience by inundating you with pop up ads. Some of the latest exploits include Cryptolocker and Cryptowall which are variations of ransomware that behave as trojans by luring someone to trigger the infection. Typically this is accomplished by enticing you to click on a program or attachment and then immediately encrypts files on your local computer as well as the network file server you connect to resulting in the screen shot below that you would normally see pop-up once the infection has applied itself. If you have seen this image before, you know that it's bad news.
Common methods of infection:
The most common method for infection is an email attachment. Once the email virus filters were able to identify and remove the infected attachments, the writes of the crpyto variations came up with an even more deceptive method for delivering the infection by utilizing cloud storage repository links. This way the file would not be contained in the email itself and therefore, more likely to arrive in the intended victims inbox and ultimately run by the unsuspecting recipient of the message.
4 Common methods of prevention:
- Firewall- This is the perimeter device or software that could prevent some infections with early detection before an infection reaches your system. Not just any firewall will provide sufficient protection for your equipment. The firewall will need to have effective web filtering services that must be configured properly and must also be current on it's protection updates. Even when a good firewall is in place and kept current, it's easy to void many of the protections provided by opening up a particular site or service at the first request of an employee that needs to access specific content on the internet.
- Email filtering- This one is self explanatory in that it filters the emails you send and receive for virus, malware, trojans, ransomware etc. Again, a reputable vendor, proper updates and proper management are critical for this service to be effective for your business and employees.
- Antivirus agents- This would be the most common protection measure in place today. This is typically software installed on your local system that utilizes a signature file to determine what is safe and what is not regarding files and applications.
- User rights restrictions- Preventing your employees or peers from logging into their desktop, laptop etc. with administrative permissions is an additional method of minimizing risks relating to infections. The reason for this is the damage is typically limited as it most commonly runs as the user that is logged in currently. If that user does not have rights to install applications or change important files, then the damage is typically limited much more than if the user has administrative rights on the local computer or resource.
- File and system backups- Essential to every business is a backup solution that will allow you to recover not only files but entire servers and, if necessary, critical desktops or laptops in the event of failure or in this case an infection.
6 Advanced methods of prevention:
- Advanced Firewall Settings- Early crypto variations utilize Tor as their traffic method to communicate back to the controlling encryption and infection vector sources. Later versions seem to have adopted the i1P and i2P traffic methods for communication. Here a few ways to reduce risk for these types.
- Utilize 3rd Party Applications- CryptoPrevent is one of the most utilized applications for reducing the risk of Crypto variation infections.
- Visit their website and review their prevention features (https://foolishit.com/)
- OpenDNS has a good reputation for providing prevention through predictive intelligence (https://www.opendns.com/)
- Eliminate Mapped Drives- Currently, most of the variations of Crypto utilize mapped drives. One way to reduce the risk of having server files encrypted is to eliminate the use of mapped drives all together. Here is one way to do so.
- Define network shares and assign group membership to the share.
- Setup a group policy to add the network share to particular domain group members
- User education- This is probably the single most important form of prevention while remaining the least utilized. Knowledge is power! And in this case, it can mean the difference between a painful infection and effective avoidance. Knowing what to anticipate and how to react to most common scenarios for infections can save you and your business a lot of heartache. Be sure to educate yourself and your employees on best practices for email attachments and web content exposure. There are may programs that provide useful content in the form of video, written assessment and user tracking for completion and score to determine if your company is educated regarding cybersecurity risks. It's a different world now and it's important to understand how to protect yourself from it.
- Predictive intelligence- This is a more advanced level of protection that involves "big data analytics" and behavioral intelligence of internet activity that predicts risks based on internet behavior patterns. This is available in only a few product lines today but can add a very effective layer of necessary protection for all of your resources.
- Application restrictions- This is a less common method of protection in that it involves much more effort. This is typically managed by creating Group Policies on a windows domain network and defining what applications are allowed to be installed and what application files are allowed to even run.
- Block TOR traffic sources and destinations
- Typically accomplished by enabling web filtering on SSL traffic & blocking “Anonymizers” & “Anonymizer Utilities” within your firewall.
- Block i1P traffic
- Block i2P traffic
- Block traffic source and destination from other countries
At Superior Solutions, we incorporate a very specific recipe that includes all of the above protections for our clients in order to enable our service teams to focus on prevention as apposed to reaction. If you are interested in finding out about how we might help your business develop successful Cybersecurity protection measures, please feel free to call or email today!
* Bonus Offer- Free advanced secrets on how to prevent and protect against some of the most recent Cryptolocker and Cryptowall variations!
[one-half-first]
[gravityform id="6" title="true" description="true"]
[/one-half-first]
[one-half]
[/one-half]
If you found this article to be useful please feel free to share using the links provided below!